Segmented hashing for imaging damaged drives
Traditionally, to verify that a drive’s image is an exact bit-by-bit copy of an evidence device, regular linear hashing is used. This method produces a single hash for the entire drive image.
But if an evidence drive has any damages, the standard linear hashing would stop after encountering the first bad sector. Therefore it is impossible to calculate a linear hash for a damaged device.
Even if an evidence device has no errors when you image it, in the future data in the image may get corrupted, and you’ll get a hash mismatch when verifying the regular hashes. So it would be impossible to prove that your image is a forensically sound copy of an evidence drive.
Segmented hashing is the solution for both verifying images of damaged evidence drives and ensuring resiliency against possible data corruption over time.
What is segmented hashing?
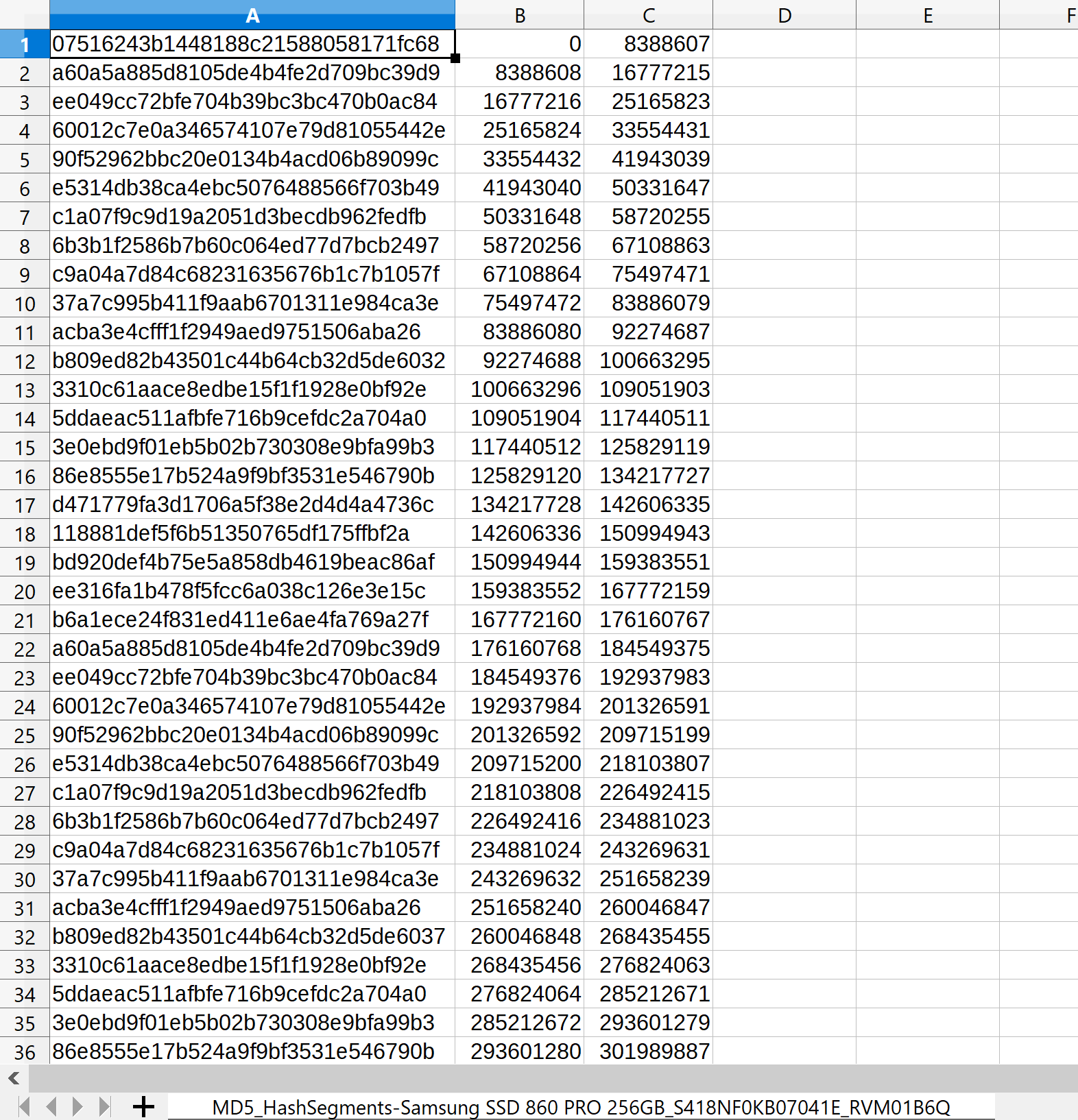
Segmented hashing is an alternative hashing method designed by Atola Technology specifically for forensic imaging of damaged drives. This method produces a multitude of hash values for individual segments (LBA ranges) of the evidence drive and the image.
Depending on imaging settings, segment size can vary from 4 to 32 GB. A new segment begins with the first sector following either the previous segment or a bad sector. And the list of these segments represents the entire image. By verifying all hashes in a set you can prove the data integrity of the entire image.
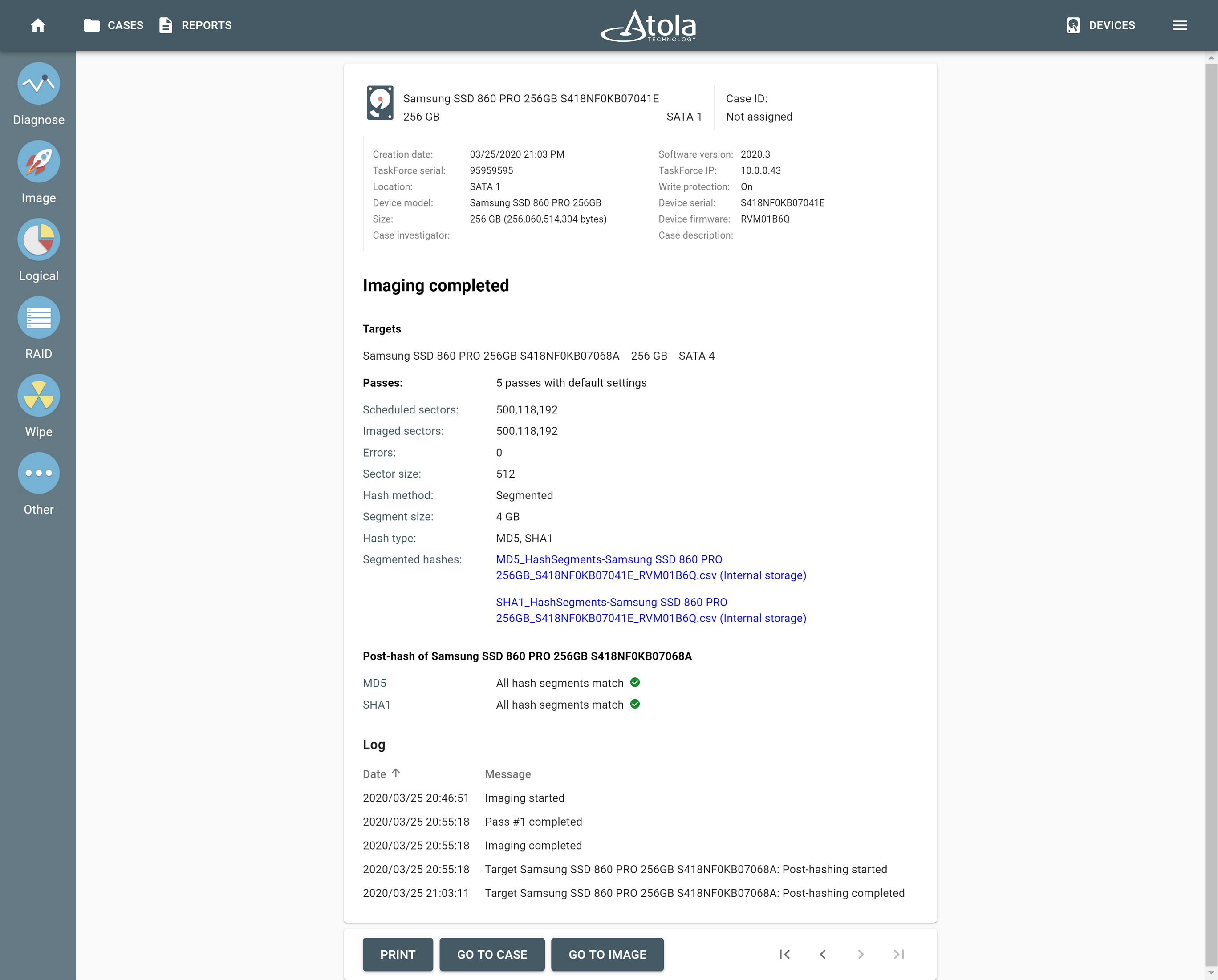
The result of segmented hashing is a CSV file where each line contains a hash value, start LBA of a segment, and end LBA of a segment:
Benefits of segmented hashing
Segmented hashing offers two main benefits: the capability to verify data integrity when imaging damaged evidence drives and the resiliency against possible data corruption in the stored images.
Verify data integrity when dealing with bad drives
Segmented hashing helps you prove successful and correct imaging of an evidence drive in a bad condition. Segmented hashes can be calculated in the process of multipass imaging of a damaged drive.
When dealing with bad drives, segmented hashing is performed only for the areas that have been successfully imaged, and all the bad sectors are omitted.
This way segmented hashing makes imaging of damaged drives verifiable and more efficient.
Secure better resiliency against data corruption
Even if an evidence device is in perfect condition at the time of imaging, the bit-by-bit copy of it you acquired may be damaged in the future. If you try to verify a corrupted image with a standard regular hash, you will get a hash mismatch and won’t be able to prove data integrity.
Segmented hashing lets you prevent that from happening because only the hash for one segment in the set will become invalid and the hashes for all the other segments can still be verified.
Potential disadvantages
The only potential disadvantage of segmented hashing compared to linear hashing is its low support in third-party tools. To overcome this issue and simplify the verification of segmented hashes, we developed a free open-source software: seghash on GitHub.
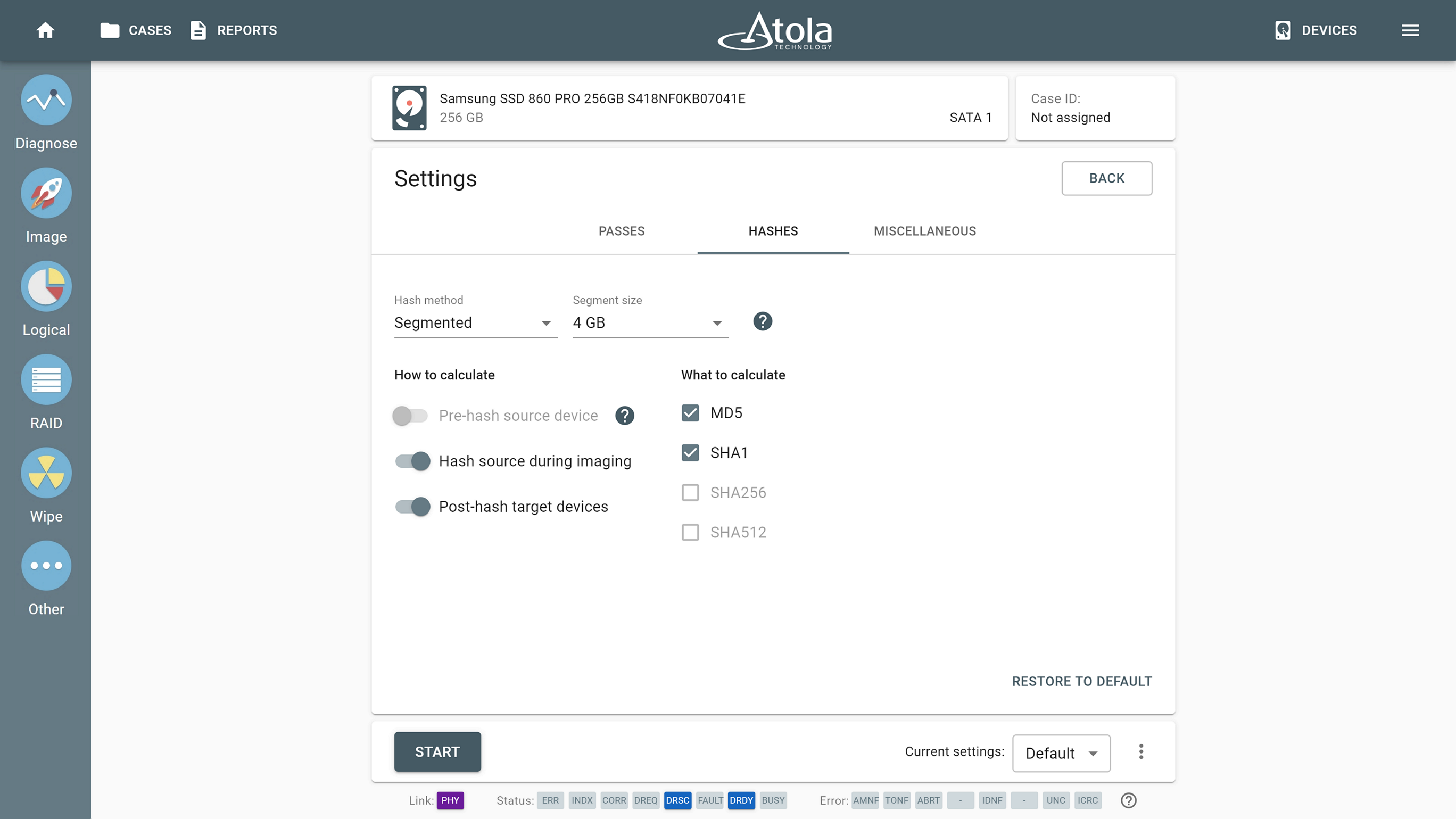
The use of segmented hashing during imaging and instant verification of a target
Go to the imaging settings and select the segmented hashing method. Toggle Post-hash target devices to calculate hashes for both the evidence drive and its image.
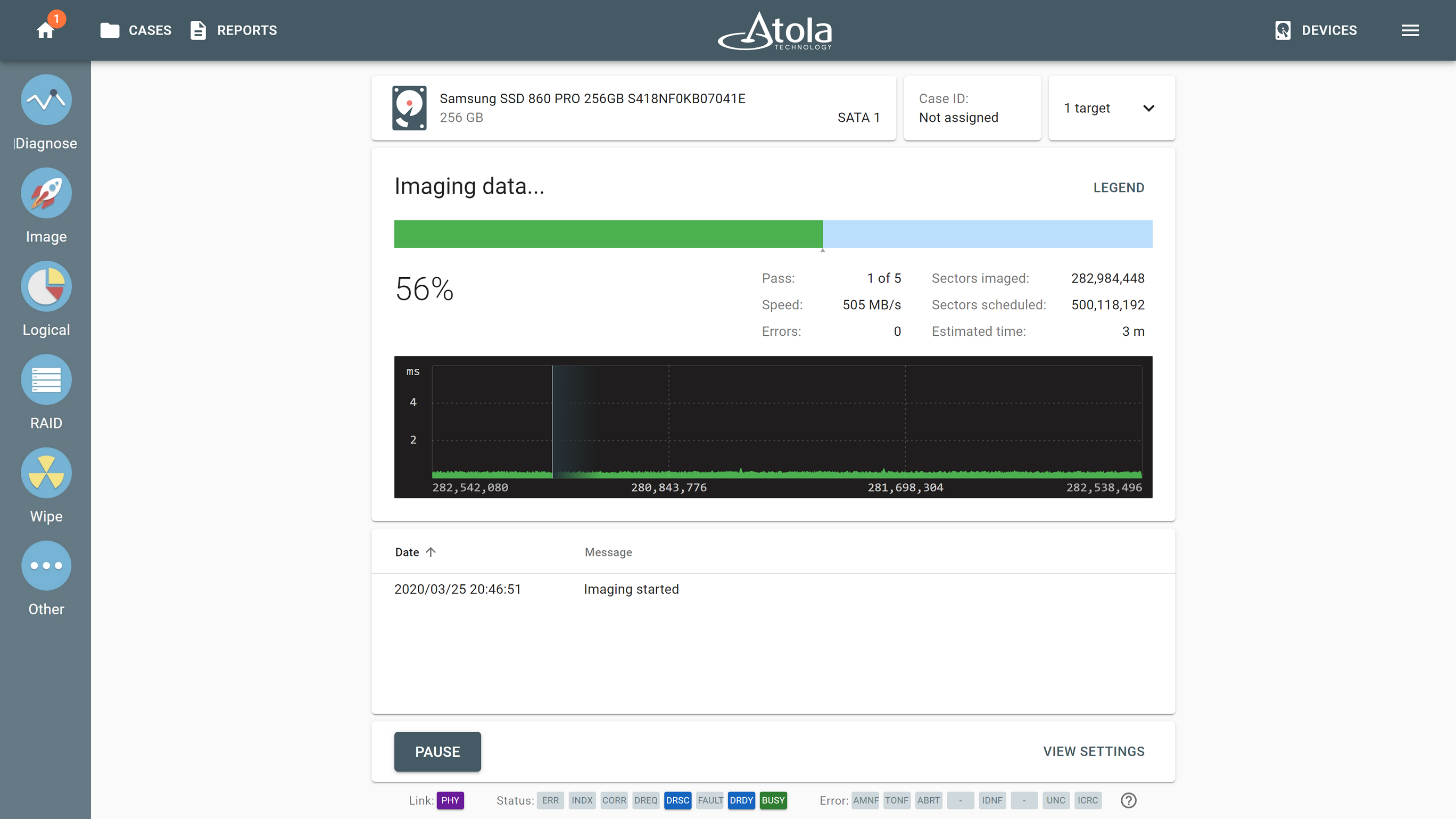
Hash calculation during imaging does not slow down the session thanks to TaskForce's highly optimized imaging and hashing algorithms:
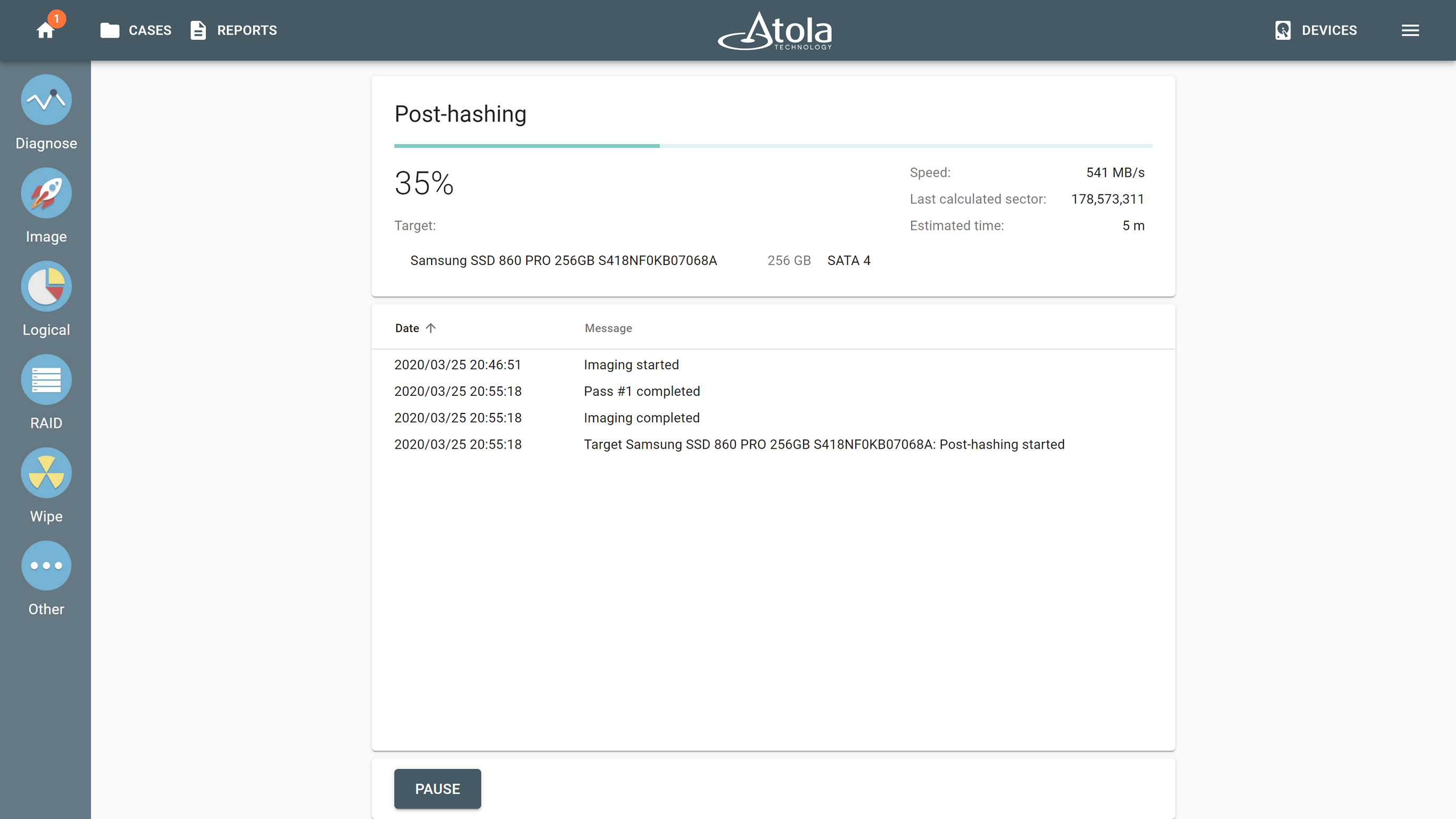
Post-hashing will commence as soon as the imaging session is completed.
The link to the CSV file with segmented hashes can be found in the Imaging completed report. If the post-hashing of the target was enabled, you also receive the results of cross-checking between the hash sets of the evidence drive and the image.